The most common type of cybercrime is phishing emails, and although many businesses and users are aware of their dangers, many staff still aren’t trained how to spot them – making them one of the most successful cyberattack vectors still.
According to Proofpoint’s 2022 State of the Phish Report, a significant 83% of organisations fell victim to a phishing attack in 2021, and Verizon’s 2021 Data Breach Investigations Report stated that 25% of all data breaches involve phishing.
So just how easy it is to fall for a phishing scam, and what should you and your teams be looking out for?
1. It’s from a free email account.
1. Reputable businesses will not send professional emails from a free email account such as yahoo.com, gmail.com or google.com. If your email is from a free email account, you should automatically be cautious.
Most businesses will communicate with their own domain and company accounts. For example, legitimate emails from Allianz will be from their domain @allianz.com, and emails from Siemens will use their @siemens.com domain. Should this format be used, the message is much more likely to be legitimate.
If the rest of the email is incredibly well designed, it would be easy to overlook the email address, but don’t.
Always check the senders email address to verify authenticity.
2. It’s not quite the right domain name
Another sneaky and easy-to-miss way that cyber criminals try and deceive us is with spelling mistakes! Attackers that might want to mimic microsoft.com for example, may have bought the domain micr0soft.com or microssoft.com; domain names so similar that the recipient simply misses the misspelling.
Here's a visual example:
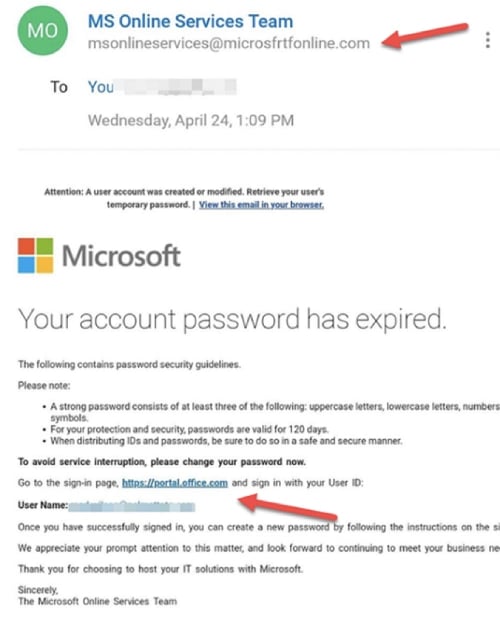
In this example the cyber criminals registered the domain ‘microsfrtfonline.com’, an easy to miss difference if you’re skim reading your emails.
Believe it or not, cybercriminals aren’t always deterred by an unsuccessful first attempt; they often gain access after multiple tries. With each failure, the criminal is learning more about the most effective methods for a successful attack.
It only takes one person to click on a malicious link for a cybercriminal to gain what they need and complete a successful cyber-attack. With criminal methods constantly adapting and evolving, it’s important that businesses ensure all employees undertake regular phishing training.
3. There are mistakes and spelling errors
In a large-scale attack, criminals can distribute thousands of phishing emails at once to unsuspecting people; they’re not too worried about errors as it only takes one victim to make an attack successful. Many cyber criminals will also target international victims, and while they might try to translate their emails into their targets’ native language, they often make several spelling or grammar mistakes in the process: another tell-tale sign of a phishing email.
On the other hand, not all of these errors are accidental, and many phishing scams contain deliberate errors and spelling mistakes. These are suspected to be part of the cyber criminals’ ‘filtering system’ - to ensure that they target only the most gullible victims. Someone who doesn’t pay attention to details is more likely to believing a bogus email is legitimate, for example, or click on a malicious link.
Bear in mind that errors don’t automatically mean that an email is bogus – everybody makes mistakes. So keep an eye out for the other symptoms too, and if in doubt, don’t click on any of the links in step 4….

4. There are dodgy links or an attachment
All phishing emails serve a purpose, and that is to obtain sensitive or useful information; anything from passwords and access details, to payment and credit card information. To do this, cyber criminals first need the recipient to click on a malicious link, open an infected attachment or download malware. These malicious files are often disguised as an invoice, a bill, a receipt or an ‘urgent’ file.
Don’t open an attachment until you’ve thoroughly checked the email for signs of phishing, are confident about the sender’s authenticity, and are expecting the email.
You can always call the sender and ask for confirmation of legitimacy.
5. Now! Important! Urgent!
If an email is demanding or strongly encouraging you to take action, click the link, or open it urgently - sit back, and double check. Scammers are hoping to scare you into making a mistake, so double and triple check any urgent emails before clicking on anything!
Hackers are hoping that you’ll be less vigilant if an email appears to have come from a boss or other authority - especially if it’s a vital request. These are sneaky phishing scams because they lure the recipient into believing it must be legitimate. Despite suspicions, no one wants to ask their boss if it’s a ‘real’ request, as this will be suggesting that their email is poor quality and looks like a phishing email.
Protect your business from phishing attacks
To combat the threat of phishing, organisations must have effective cyber security measures in place and provide regular staff awareness training.
It’s only by reinforcing advice on avoiding scams that your team can develop good habits and detect malicious messages efficiently.
If you’d like to learn more, get in touch, we're happy to help.